Improve your security with the integration of AWS Control Tower and AWS Security Hub

The authors are pleased to announce the general availability (GA) of the integration between AWS Control Tower and AWS Security Hub. In this GA release, AWS Control Tower can detect control operations performed on Security Hub discovery controls from the Security Hub service. This includes detecting whether Security Hub controls enabled by AWS Control Tower are disabled directly from the Security Hub. When AWS Control Tower detects a control that has been disabled in the Security Hub, the deployment status of each affected control will be displayed as 'Drifted.' To do this, you have to go to the Security Hub service for individual managed AWS Control Tower accounts to check the status of those controls. This created an extra step and the risk of unintentionally disabling the control. With the introduction of this drift detection feature, you can now monitor the status of control deployments. You can then take appropriate action to manage the security status of your AWS Control Tower environment from within the AWS Control Tower service.
AWS Control Tower controls, including controls belonging to the Security Hub, are mapped to associated control targets in the AWS Control Tower control library. This provides a view of the controls required to meet a specific control objective. For example, the Enforce least privilege control objective is currently mapped to 63 controls, 30 of which are Security Hub member controls. You can view the list of control targets for more information on AWS Control Tower control targets. Combining over 170 detective controls from Security Hub with the automation of AWS Control Tower's multi-account environments gives you a baseline for management as you scale.
In this article, the authors will configure the integration between the AWS Control Tower and the Security Hub to demonstrate drift detection. This will include enabling Security Hub detection security with AWS Control Tower. You will then be able to display the control compliance status for all findings in the Security Hub.
Integration Overview
To integrate Security Hub with AWS Control Tower, start by enabling the detection controls belonging to Security Hub in AWS Control Tower. A new Security Hub Service-Managed Standard is created when you first enable controls in an organizational unit (OU) managed by AWS Control Tower. This applies to all accounts managed by that OU. Thereafter, all controls belonging to the Security Hub you enable from the AWS Control Tower in this OU will be handled in this standard. AWS then recommends enabling or disabling these controls from the AWS Control Tower. If you disable a control in this standard directly from the Security Hub, AWS Control Tower will detect this and set it as a 'Drifted' state. To fix the detected drift, you must re-register the business unit in AWS Control Tower or disable and enable the control from the business unit.
Integration flow
Figure 1 below shows the integration workflow between AWS Control Tower and Security Hub.
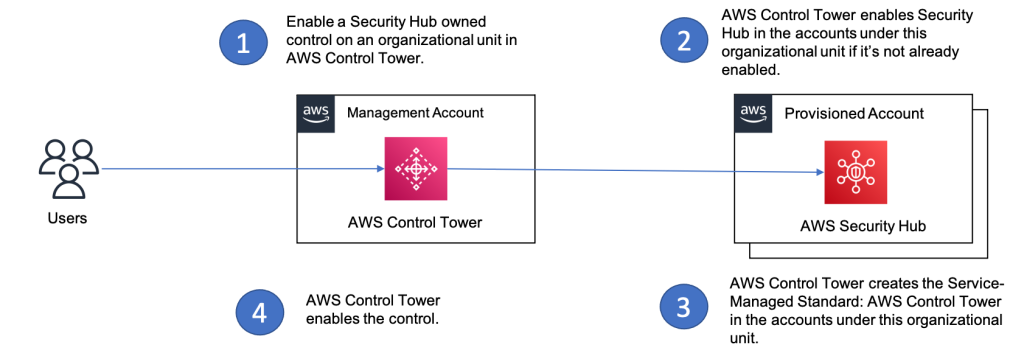
Drift detection flow
Figure 2 below shows the drift detection workflow. In this example, drift is included after the Security Hub control that was initially enabled from AWS Control Tower has been disabled.
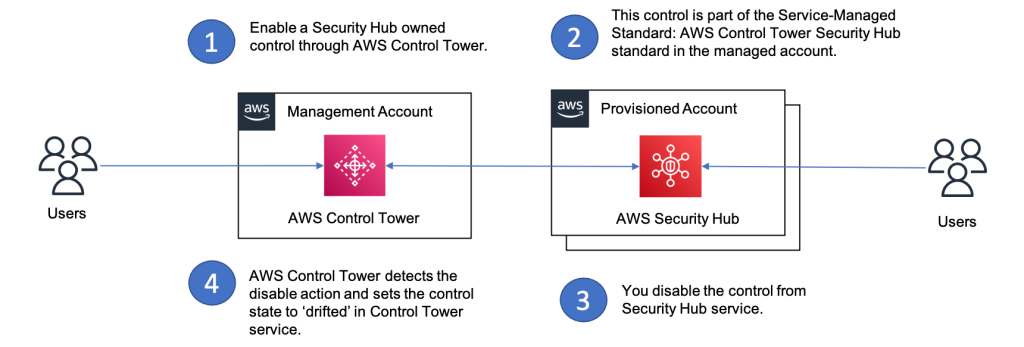
Next steps
Prerequisites
- Update your AWS Control Tower target zone version to version 3.2 to enable drift detection. For more information, see Updating the target zone.
Steps to integrate AWS Control Tower and Security Hub
The following steps integrate Security Hub with AWS Control Tower.
- Go to the AWS Control Tower console and click All Controls in the left pane.
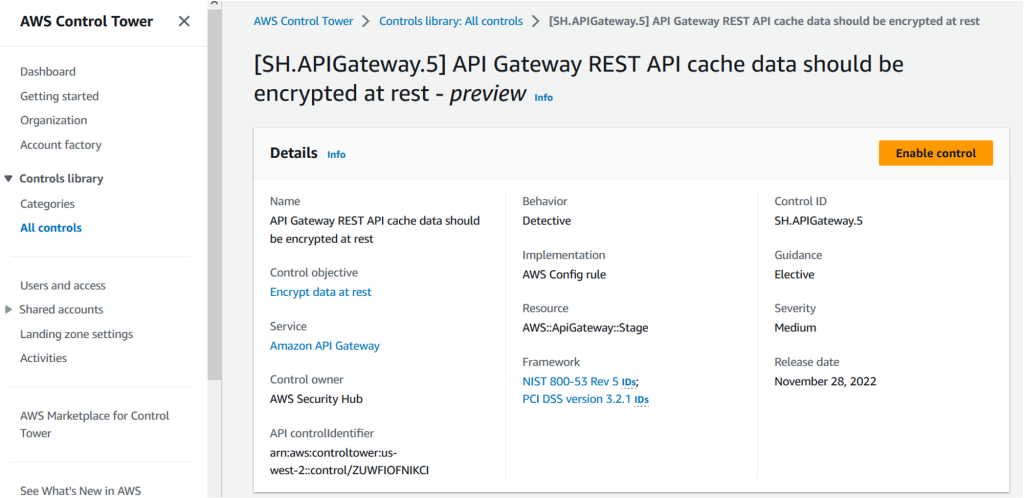
- Select the controls that belong to the Security Hub. In this example, [SH.APIGateway.5] API Gateway REST cache data should be encrypted at rest.
- Click Enable Control.
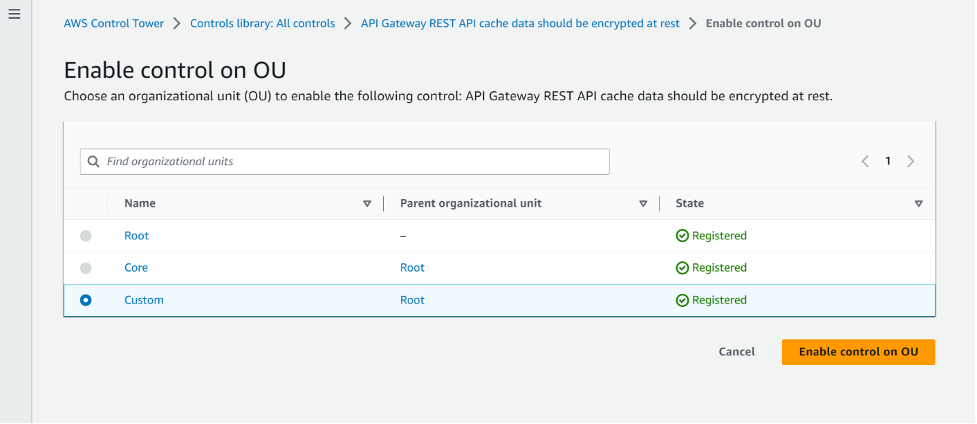
4. Select the organisational unit for which you want to enable this control. For example, the authors have selected a Custom OU.
5,. Click Enable control on OU.
6. Log in to the managed account within the organizational unit selected in step 4.
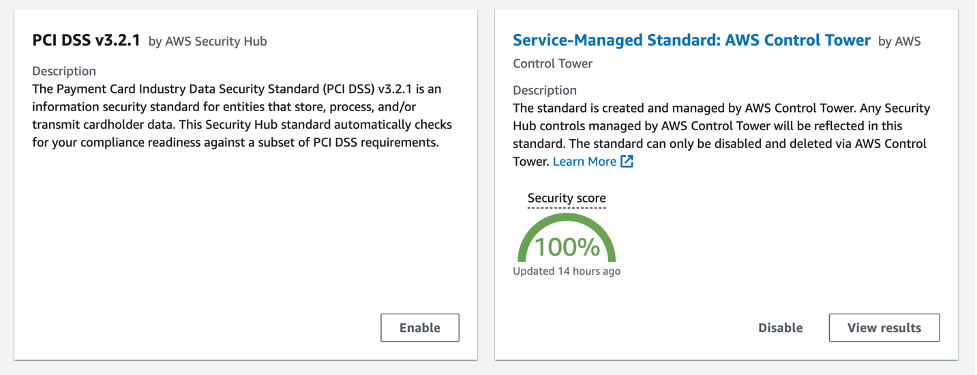
7. Go to the Security Hub console and click Security Standards in the left pane. Click Service-Managed Standard: AWS Control Tower to see the control enabled in step 2.
8. In Figure 5 below, you can see the managed AWS Control Tower standard in the Security Hub; the control enabled by the authors is part of this standard.
The previous steps showed how to enable Security Hub controls via the AWS Control Tower console. You can also help with these controls using the AWS CLI or AWS Control Tower control API operations.
You can use this AWS CLI command to enable the controls:
aws controltower enable-control --control-identifier <ARN_of_the_control> --target-identifier <ARN_of_the_OU>The code snippet below shows how to allow AWS to Control Tower controls via the Python Boto3 API. Please refer to the control enablement documentation for more information on this API.
At this point, you have successfully activated the integration between AWS Control Tower and Security Hub. From the next section, you will learn how the drift detection function in AWS Control Tower works for controls belonging to the Security Hub. The authors will use the same power they enabled in the previous steps.
Steps were taken to test the drift detection workflow
- Log in to the member account from the previous section with the control enabled.
- Go to the Security Hub console and select Security standards from the left panel.
- Click Service-Managed Standard: AWS Control Tower, which will show the control you enabled in the previous section.
- Click the control and then click Disable Control. Figure 6 below shows how you can disable this control.
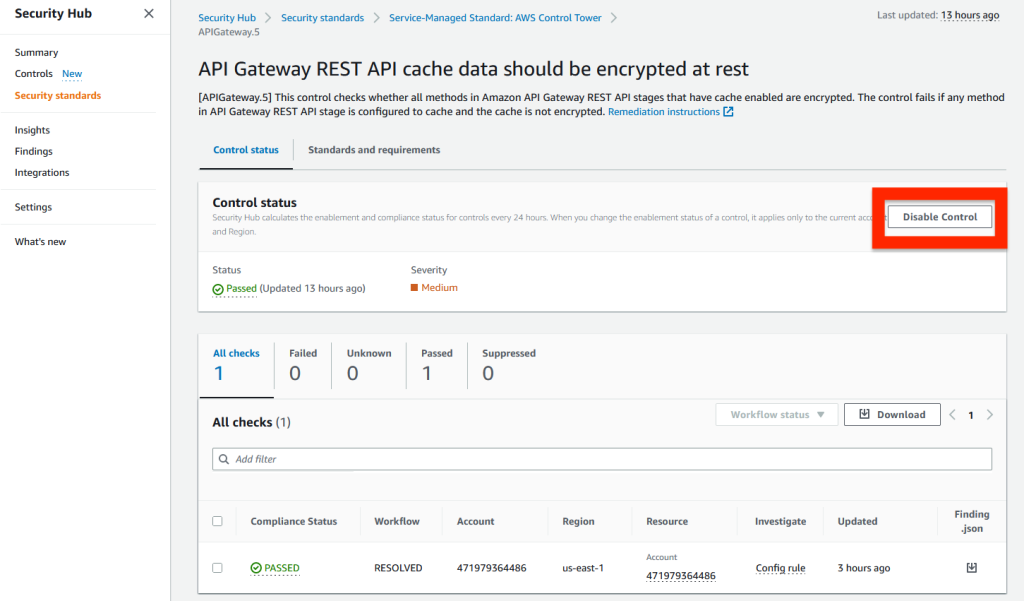
- Select one of the reasons from the drop-down list and click Disable. This action will set the control to the 'Drifted' state in the AWS Control Tower.
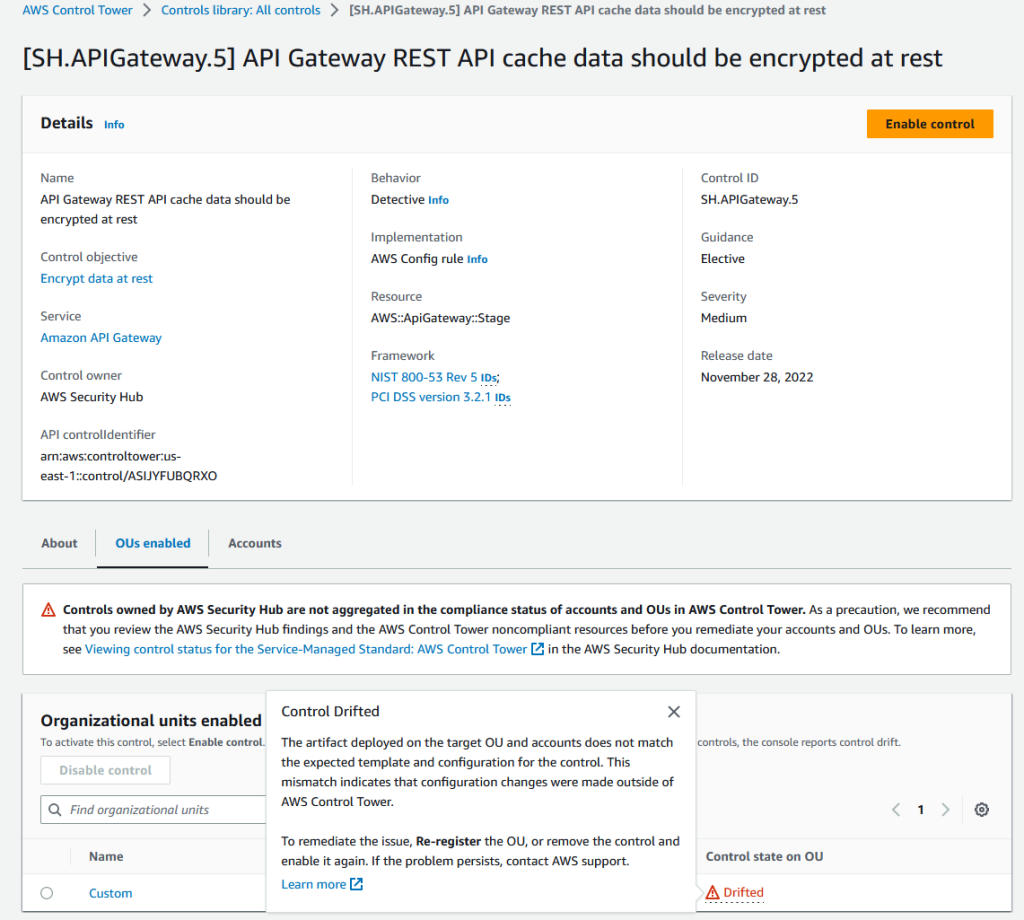
- To see the 'Drifted' state, go to your management account's AWS Control Tower console and select All Controls in the left pane. Search for the SH.APIGateway.5 Control and click the OU tab. You should see the control state in the OU as Drifted, as shown in Figure 7 below
Tidying up
To remove Service-Managed Standard: AWS Control Tower from accounts where controls belonging to the Security Hub have been enabled, you must disable these controls from AWS Control Tower. This applies to all accounts in this business unit. Removing a standard does not deactivate the Security Hub on your account.
Using Security Hub to view the compliance of discovery controls
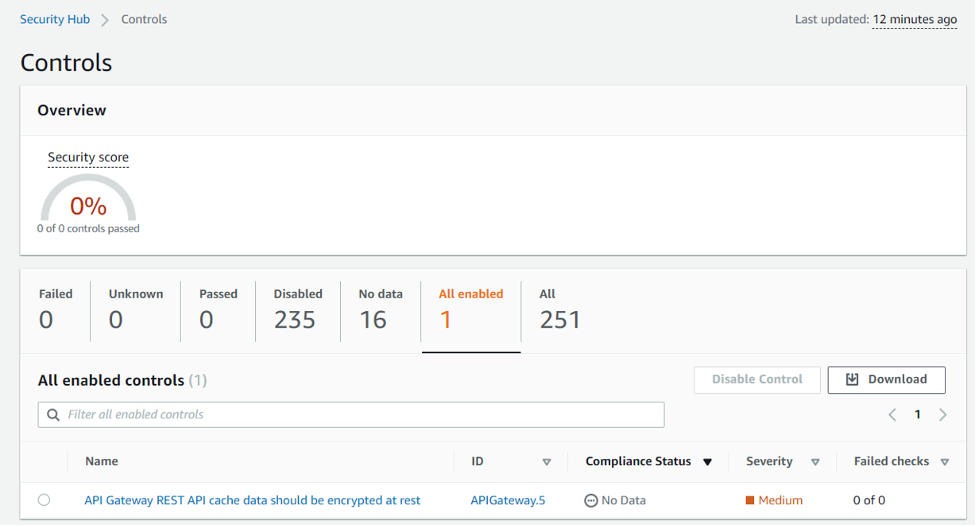
Once you have configured discovery controls via AWS Control Tower, you can use Security Hub to discover existing misconfigurations in your accounts. You cannot view the compliance status of Security Hub discovery controls in AWS Control Tower. In Security Hub, you can view these findings and compliance status at both the individual account and organization levels.
To view the results for a specific control that AWS Control Tower has activated via the Security Hub console:
- Go to the Standards page.
- Access the 'Service-managed standard: AWS Control Tower' standard.
- Access the control whose results you wish to display.
- A list of results will be displayed at the bottom of the page.
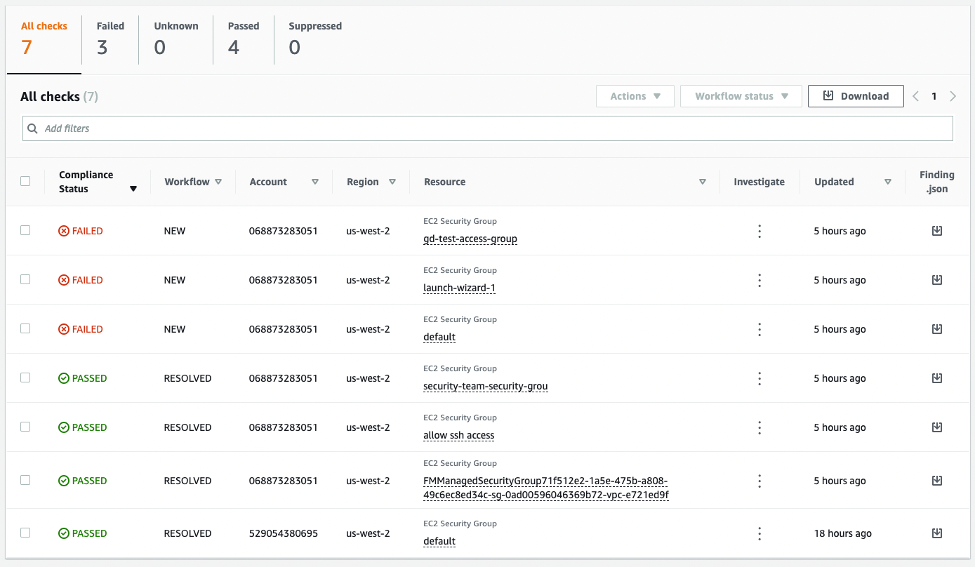
Alternatively, you can use the GetFindings command via the API or CLI.
You can set up aggregation between regions in the Security Hub to view all results in one area. Now, you can view all results simultaneously without switching between regions. For further information, see the Security Hub documentation.
Conclusions
From this article, you have learned how to integrate, enable, and manage Security Hub controls from AWS Control Tower. The developers demonstrated AWS Control Tower drift detection for controls belonging to the Security Hub. They showed how to use Security Hub to display the results of these controls across the AWS organization. With this publicly available feature, you can use Security Hub as a single place to detect misconfigurations when managing large-scale AWS Control Tower environments.



