Tag workloads with AWS Config compatibility packages on AWS accounts

General overview
As cloud deployments become more complex, organizations struggle to manage and identify a growing set of resources. Tags provide companies with metadata about their resources, which they can use to identify resources for cost allocation, operations, or data security.
AWS Config is an AWS service that continuously assesses, inspects, and evaluates the configurations and relationships of your AWS resources. It enables you to detect existing resources in your account, record their configuration, and capture any changes, allowing you to resolve operational issues quickly. In addition, using predefined, customizable AWS Config rules, you can assess whether your AWS resources comply with typical best practices and optionally configure corrective actions for non-compliant resources using AWS Systems Manager runbook elements. One such managed rule, required-tags, is a rule that checks that resources have specific tags that you identify. For example, with this rule, you can check whether your Amazon Elastic Compute Cloud (Amazon EC2) instances have a CostCenter with a tag key.
Solution outline
In this article, the authors provide an example of a customized Runbook element of the Automation service, an AWS Systems Manager capability that automatically corrects incompatible resources evaluated by the required AWS Config rule tags. This is particularly useful in a multi-account environment where similar requirements are shared across multiple AWS accounts. As AWS Config and Systems Manager are regional services, you must implement this solution in each region on each account that requires it.
The developers will start by guiding you through creating a shared AWS Systems Manager Automation runbook component from an AWS management account. Then, they will show you how to make it available to member accounts in your AWS organizations. They will then combine the required AWS Config tag rule and remediation action using the runbook automation element of the AWS Config compliance package. The Compliance Pack is a collection of AWS Config rules and remediation actions that can be easily deployed as a single unit in an account or across an organization. Finally, they will deploy it through the AWS organization to selected AWS accounts.
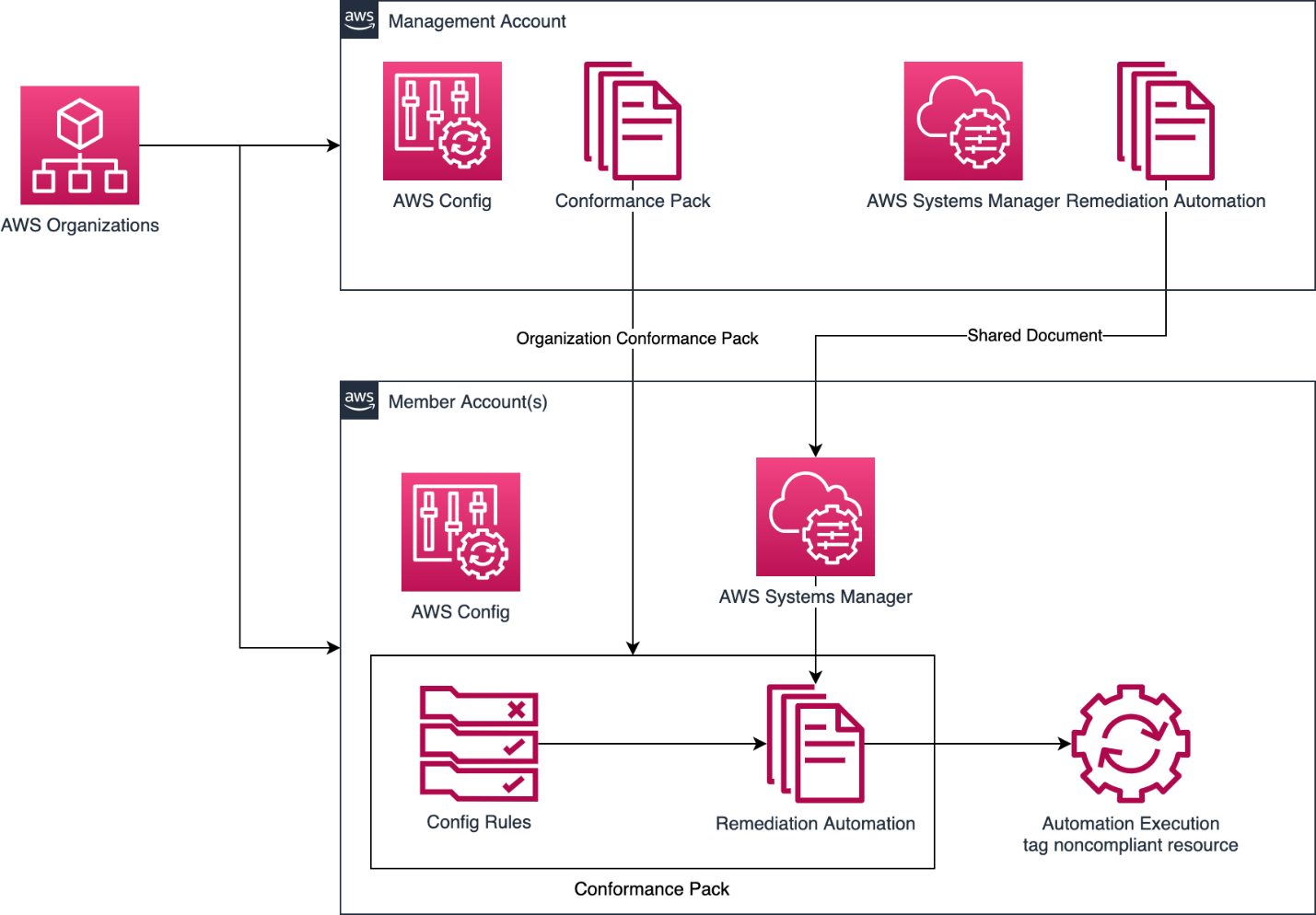
Please note that this solution will only work with services supported by the Resource Group API. A list of supported services is available here.
Services used in this solution
AWS Config provides a detailed configuration view of AWS resources in your AWS account. This includes how resources are related and how they have been configured in the past so you can see how configurations and relationships change over time.
AWS Systems Manager is a secure, end-to-end solution for managing hybrid cloud environments. Developers will use it to automatically correct incompatible resources using the Runbook element of the Automation service.
AWS Organisations enables the creation of new AWS accounts at no additional charge. Organizational accounts allow you to efficiently allocate resources, group accounts, and apply governance rules to accounts or groups. In this text, the authors will use AWS Organisations to show how easy it is to use AWS Config and AWS Systems Manager in a multi-account environment.
Prerequisites
In this tutorial, you must enable AWS Config on all accounts in your AWS organization. A quick way to allow AWS to configure recording is to use Quick Setup, a capability provided by AWS Systems Manager that will enable you to create a configuration recorder quickly.
This requires that the company name tag key and company XYZ tag value be added to all EC2 instances in the selected accounts in your AWS organization. Prepare the following information before proceeding with the guide:
- AWS Organisations Management account ID.
- (Optional) A list of member account IDs that you want to exclude from deploying this solution.
- The Amazon Simple Storage Service (Amazon S3) resource in your AWS Organisations Management account will store the compliance package template.
- You will be using AWS CloudFormation and stacks. Check out the documentation here or this video introduction.
Implement the IAM role using CloudFormation
Below is the CloudFormation template the authors use to create the IAM role required to trigger the remediation action they make later in the 'Create the Automation runbook' section. You will first deploy this as a StackSet from a management account to member accounts in your organization. You will then use the stack to deploy to the management account, as StackSets are not deployed to management accounts.
First, deploy the CloudFormation StackSet. Open the following GitHub page and download the cf-iam.yaml file.
- You can optionally change the IAM role name and/or policy name in the CloudFormation template. For the purposes of the text, the name of the IAM role will be TagRemediationAutomationRole, and the name of the policy will be TagRemediationAutomationPolicy.
- In your manager account, go to the AWS CloudFormation console and select StackSets from the menu on the left.
- Click Create a stack set.
- Leave the default settings for the Permissions and Prerequisites - Prepare the template section on the Select template page. Select the Submit template file in the Specify template section and then navigate to the cf-iam.yaml file you downloaded earlier. Click Next.
- On the Specify StackSet page, name the StackSet (for this text, call it StackSetIAMRoleForRemediation). Leave the rest of the screen with the default settings. Click Next and then Next again.
- On the Set Deployment Options page, in the Specify Regions field, select the region where you want to deploy this StackSet. Select us-east-1 for the purposes of this article. Leave everything else with the default values and click Next.
- On the Review page, again leave everything else at defaults, scroll to the end of the page and tick the box next to I acknowledge that AWS CloudFormation might create IAM resources with custom names, then select Submit for deployment.
Next, deploy CloudFormation Stack.
- In your management account, navigate to the AWS CloudFormation console. Select Stacks from the menu on the left.
- Click Create Stack, then select From new resources (standard) from the drop-down list.
- On the Create Stack page, leave the default values for Prerequisites - Prepare template. In the Specify template section, select Submit template file, then navigate to the cf-iam.yaml file you downloaded earlier. Click Next.
- On the Specify Stack Details page, give the stack a name (for this text, call it StackIAMRoleForRemediation) and leave the rest of the screen with the default values. Click Next and then Next again.
- On the Overview page, again leave all the defaults, scroll to the end of the page, and tick the box next to I acknowledge that AWS CloudFormation might create IAM resources with custom names, then select Submit for deployment.
Having deployed this to your environment, you now have the required role to adopt when the Automation service runbook element is triggered by a corrective action defined in the AWS configuration.
Create an Automation service Runbook element for the corrective action and make the Runbook element available to your member accounts
Correction of non-compliant resources evaluated by an AWS Config rule is performed using Automation service Runbook elements. To maintain centrally managed Runbook elements across your organization, create this Runbook element using the CloudFormation stack in your management account and make it available to your member accounts via the AWS Management Console.
Open the following GitHub page and download the cf-automation-runbook.yaml file.
- In your management account, navigate to the AWS CloudFormation console. Select Stacks from the menu on the left.
- Click Create Stack, then select With new resources (standard) from the drop-down list.
- On the Create Stack page, leave the default values for Prerequisites - Prepare template. In the Specify template section, select the Load template file, then navigate to the cf-automation-runbook.yaml file you downloaded earlier. Click Next.
- On the Specify Stack Details page, give the stack a name (for this blog, call it StackRemediationRunbook). Leave the rest of the screen with the default settings. Click Next and then Next again.
- On the Overview page, again leave all the default settings, scroll to the end of the page and select Submit for deployment.
This template has created an Automation Service Runbook element called SsmDocumentTagRemediation, which uses the ResourceID passed by the AWS Config rules to query the ARNs of incompatible resources, and then uses the AWS Resource Group Tagging API to tag those resources.
Now that you have created an Automation service runbook element make it available to member accounts in the AWS organization. To do this:
- Open the AWS Systems Manager console in your management account and select Documents in the left navigation pane.
- Select the Owned by Me tab and the Runbook SsmDocumentTagRemediation item created in the previous step.
- Select the Details tab. In the permissions section, add any account with which you want to share this Runbook item and select Save to save your changes. (Note: there is a limit that allows a single Systems Manager document to be shared with up to 1,000 AWS accounts).
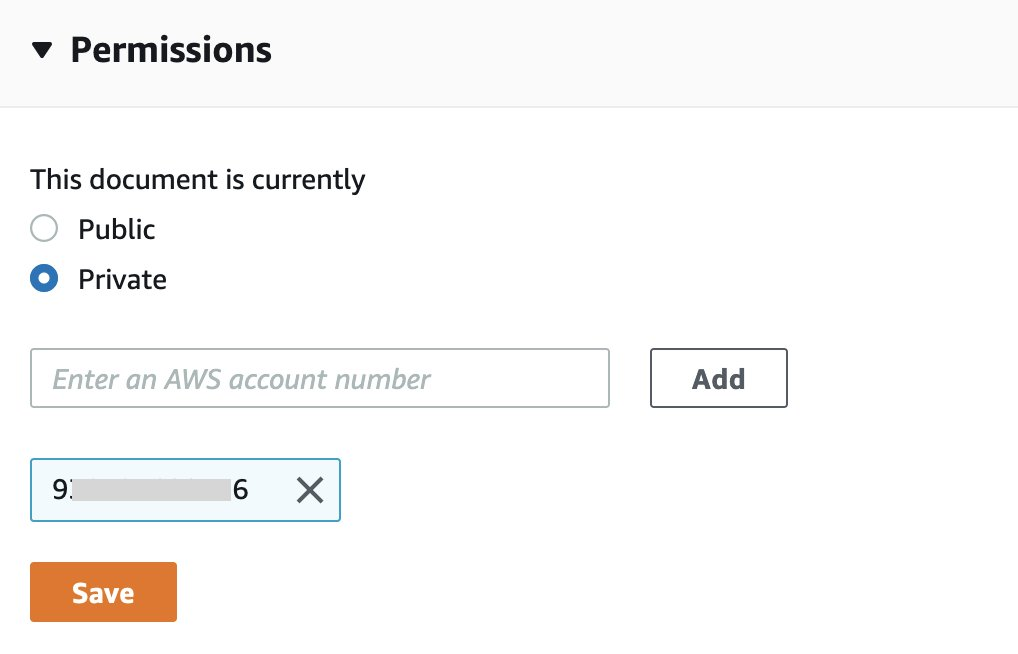
Note that while we use the console to share the Runbook element, you can also use the ModifyDocumentPermission API or AWS CLI to add AWS account IDs programmatically.
Deploy a compliance package on a management account
A compliance bundle is a set of AWS Config rules and remediation actions that can be easily deployed as a single entity in an account and region or across an organization in AWS organizations. As shown in the example discussed here, you will deploy a compliance package through an AWS organization.
For security reasons, you can deploy an organization's compliance package from a management account or a delegated administrator account. You will deploy this article from the management account.
To deploy a compliance pack to AWS organizations, you can use the put-organization-conformance-pack command of the AWS command-line interface (CLI) or AWS CloudFormation. In this article, the authors will create a compliance pack template and send it to the S3 tray, then deploy the organization compliance pack using the AWS CloudFormation AWS::Config::OrganisationConformancePack resource.
To create a compliance pack template, open the following GitHub page and download the cf-conformancepack-doc-map.yaml file.
- Before implementing the conformance pack, modify the conformance pack template to suit your needs. In this example, the authors specify that their resource requires the following tags and compliance package names:
- Tag1key: company-name
- Tag1value: company XYZ
- Conformance Pack Name: TagRemediationConformancePack
- Define the conformance pack name as a parameter in lines 19-22: Parameters: ConformancePackName: Default: 'TagRemediationConformancePack' Type: String
- The required tag/value pair is defined in lines 23-27 as a map named RequiredTags:
Mappings:
RequiredTags:
tag1:
key: company-name
value: companyXYZ
4.The required tag/value you defined in the previous step will be used to provide the InputParameters value of the ResourceTaggingCheck resource in lines 39-41:
InputParameters:
tag1Key: !FindInMap [RequiredTags, tag1, key]
tag1Value: !FindInMap [RequiredTags, tag1, value]
5. The RequiredTags map is also used to provide the value of the Parameters section of the MapTaggingRemediation resource, which will be passed to the Remediation Automation Runbook element in lines 51-58:
Parameters:
RequiredTags:
StaticValue: Values:
- !Sub
- '{"${tag1key}":"${tag1value}"'
- tag1key: !FindInMap [RequiredTags, tag1, key]
tag1value: !FindInMap [RequiredTags, tag1, value]
6. In the Scope property of the ResourceTaggingCheck element for ComplianceResourceType, you specify which services are to be evaluated by this rule. In this article, the authors specify only EC2 instances as AWS::EC2::Instance. For a list of supported AWS services, see the supported resources defined in the AWS Config User Guide under the topic required tags. Note that to add tags to a resource, you need the necessary permissions for the service to which the resource belongs, as well as permissions to add tags. The IAM role created allows Automation to add tags to EC2 instances. Suppose you want to tag resources in other AWS services. In that case, you need to add the permissions required by the relevant service to the IAM role that was deployed when you implemented the IAM role via CloudFormation StackSets and Stack. For more information, refer to the User Guide documentation for each service.
7. In the Conformance Pack template, replace your management account ID in lines 49 and 70 and change the region if you deploy the conformance pack in an area other than us-east-1 on line 49.
8. When all modifications are complete, upload the Conformance Pack template to the S3 tray in your management account. Make a note of the S3 URI after uploading. An example S3 URI looks like s3:///cf-conformancepack-doc-map.yaml.
You can specify up to 6 tag/value pairs for the managed required-tags rule. You can download a complete sample compliance package template with multiple required tags and a sample account identifier 123456789012, implemented in us-east-1.
To deploy the compliance pack as an organization's compliance pack via CloudFormation, open the following GitHub page and download the cf-org-conformance-pack.yaml file.
- (Optional) You can modify the ExcludedAccounts parameter in version 24 of the CloudFormation template cf-org-conformance-pack.yaml to specify a comma-separated list of accounts you do not want to deploy the ConformancePack.
- Modify the TemplateS3Uri in line 31 using the S3 URI of the ConformancePack template uploaded to S3 in the previous step. Note that if you changed the ConformancePackName in line 21 of the compliance-doc-map.yaml file, you must change the value of the OrganisationConformancePackName parameter in version 30 of this template to make it compliant.
- Use AWS CloudFormation to deploy this CloudFormation template as a stack from your management account:
- Go to the AWS CloudFormation console. Select Stacks from the menu on the left.
- Click Create Stack, then select From new resources (standard) from the drop-down list.
- On the Create Stack page, leave the default values for Prerequisites - Prepare template. In the Specify template section, select Submit template file, then navigate to the cf-org-conformance-pack.yaml file you downloaded earlier. Click Next.
- On the Specify Stack Details page, give the stack a name (for this article, call it StackConformancePack). Leave the rest of the screen with the default settings. Click Next and then Next again.
- On the Overview page, again leave all the default settings, scroll to the end of the page, and select Submit for deployment.
Once the CloudFormation deployment is complete, the compliance package will be deployed to all accounts in your organization except the excluded accounts.
Check the compatibility of EC2 resources for the compliance package
After following the steps above, you now have a deployed AWS Config organization's compliance package with the specified desired required tags and a remediation action that will automatically flag incompatible resources.
Verify from your management account
- Open the AWS Config console and navigate to the Conformance Packs page. On this page, you can see the previously deployed conformance pack and conformance assessment.
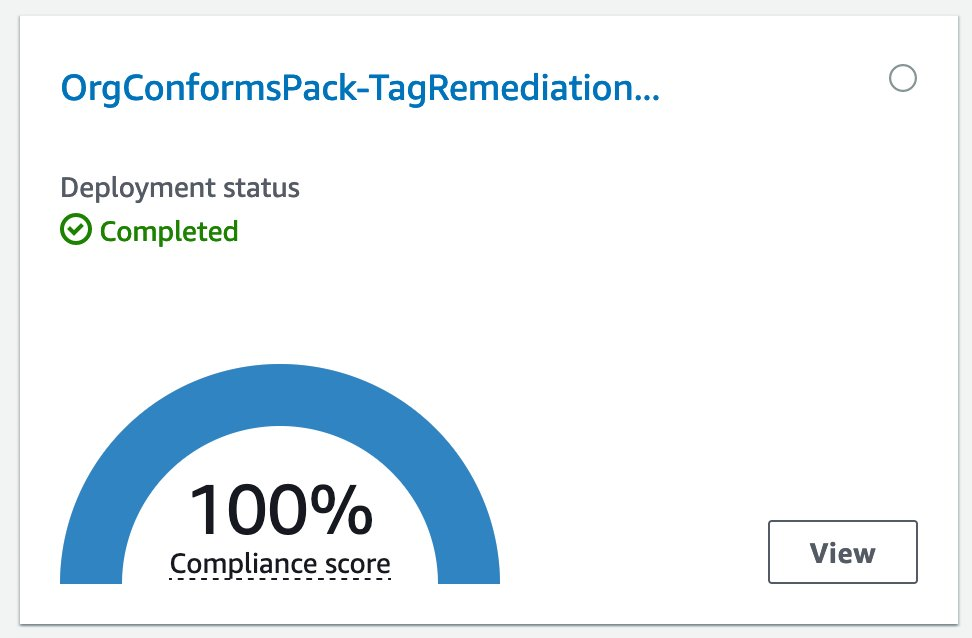
- Click the name of the conformance pack to see more details, and then see the rule deployed with the conformance pack and the conformance status of the regulations.
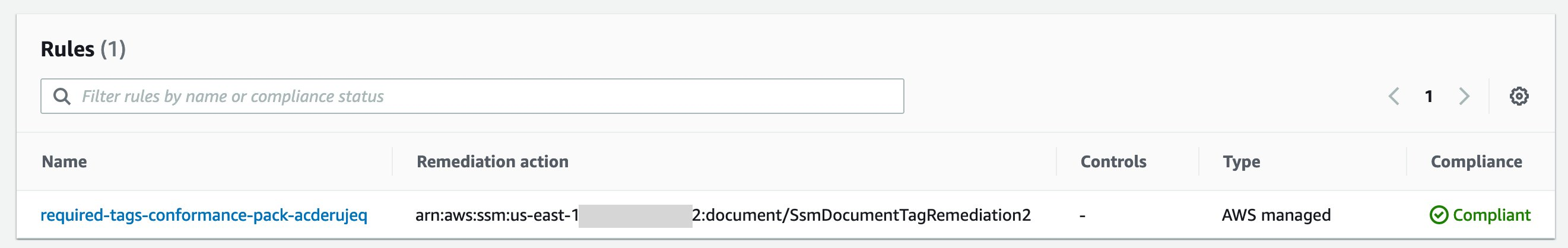
- Click the rule's name to validate the correcting action and view the resources in scope. You can also see the status of the corrective actions if they have been triggered.
- Go to the AWS System Manager to view the Automation execution history and see details of the execution or resolution.
(Optional) Validate on a member account
Log into one of the member accounts where the compliance package has been deployed and follow the steps above to verify the resource's compliance status.
Clean up
To clear the resources deployed in this post, perform the following steps in the management account:
- Remove the CloudFormation compliance package stack.
- Cancel the sharing of the Automation service Runbook element with member accounts.
- Delete the CloudFormation stack of the Automation service Runbook element.
- Delete the CloudFormation stack and stack set of the Automation IAM role.
Applications
Resources deployed in the cloud have become much more complex in recent years, and companies have struggled to manage them all properly. In AWS, tags can provide metadata about these resources. Tags can be used to identify, operate, and maintain resources, helping organizations with issues such as operations and security.
Using this article as an example, the authors showed how to use the AWS Config compliance suite to automatically tag incompatible resources assessed by a managed AWS Config rule. In particular, they focused on creating a customized Runbook element for the automation service for remediation action. They then made the Runbook element available to member accounts in our AWS organization. They then created an AWS Config compliance package that linked the AWS Config managed rule to the Automation Runbook element with the required tags. They also demonstrated how to deploy the organization's compliance package in a multi-account environment to selected member accounts in our AWS organization.
Check out the AWS Whitepaper Tagging Best Practices to learn more about tagging best practices and build a tagging strategy for your business needs.



