
DevSecOps is a cultural shift in the software industry that aims to integrate security into rapid application release cycles. This of course requires the implementation of appropriate in-team processes. Many of these, related to security, are automated and handled by the software development team itself.
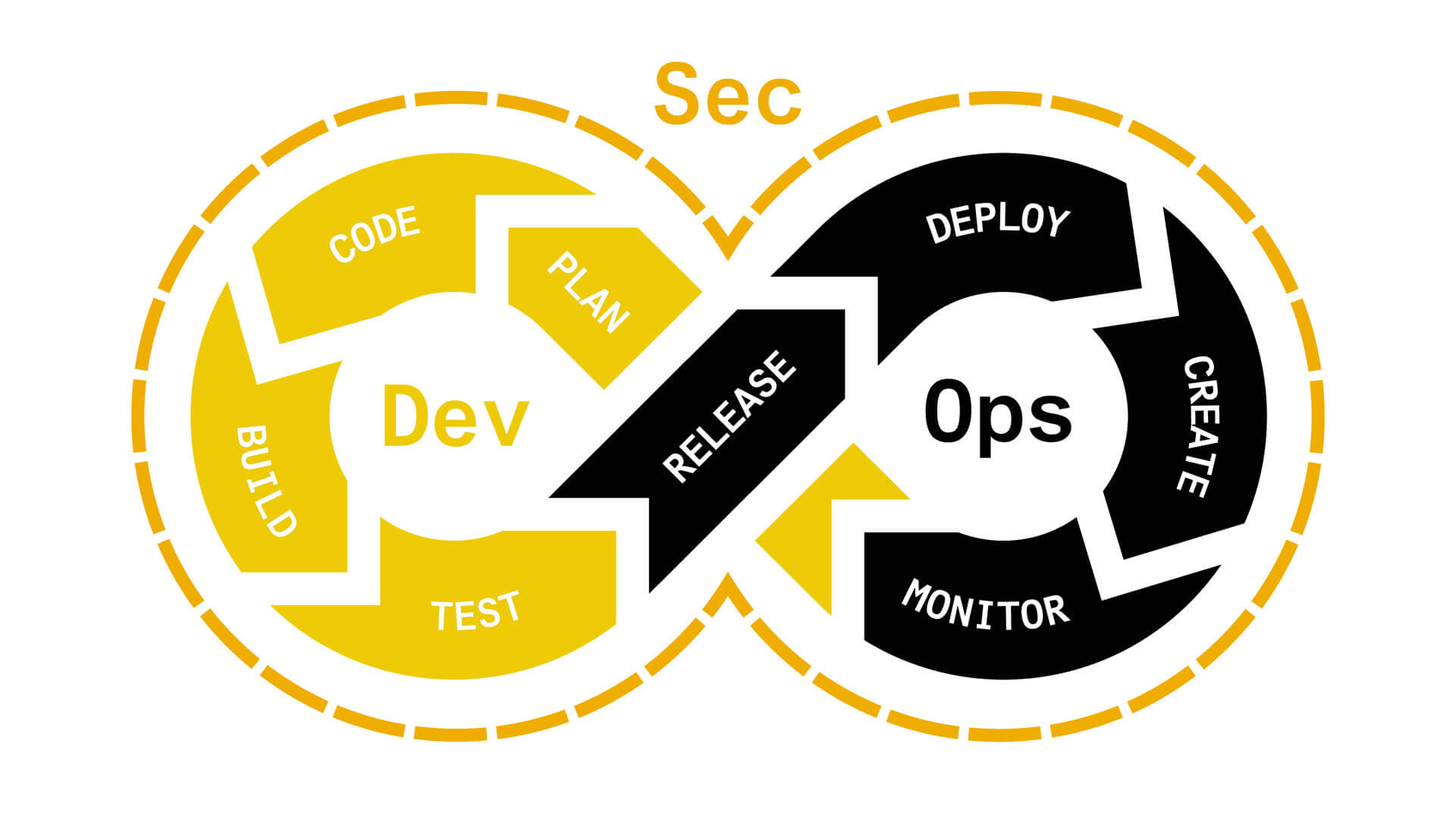
What is DevSecOps?
In the past, security was part of an isolated team with isolated processes and did not play an integrated role in application development. The DevSecOps cycle integrates all three aspects of rapid software development and includes all three key steps.
How does DevSecOps differ from traditional software development approaches?
Traditionally, software is released over a longer period of time because it has to go through a series of tests by separate security and quality assurance teams, which creates silos and contributes to longer release times.
More modern software development works with smaller deployments in a cloud-based system. Agile development practices have become more prevalent as code is deployed faster and typically in an automated manner. With new processes and tools, companies can innovate faster.
DevOps emerged as a result of new cloud deployment capabilities, but security was often overlooked in the process. DevSecOps corrects this process by implementing security testing at a higher level and as part of a continuous development cycle.
DevSecOps components
Aspects of DevSecOps include:
- Continuous Integration/Continuous Delivery (CI/CD): rapid and secure delivery of products and services within the business.
- Infrastructure as code (IaC): computing resources are responsive and flexible whenever changes occur
- Monitoring: security aspects are closely monitored at every stage
- Logging: all security events are meticulously recorded
- Microservices: large systems are reduced to smaller, more manageable components.
- Communication: the combined team can easily communicate with each other to ensure every step of the process is properly managed and necessary steps are not missed.
DevOps security is automated
Consider the entire operational and development environment, including container registries, CI/CD, release automation, source control repositories, operational management and monitoring, and API management. Organisations are able to adopt agile development cycles, which contributes to new security measures and better products.
DevOps Security is designed for containers and microservices
Containers enable dynamic and more scalable infrastructure. DevSecOps should adapt practices to container-specific security. Security must be carefully implemented at every stage of the development cycle, as cloud-native technologies don't quite meet stringent security checklists. Security should be built into every level of application development to protect the environment as well as CI/CD practices.
Why is DevSecOps needed?
New developments in IT, cloud computing and applications are constantly emerging. DevSecOps strategy can keep companies competitive and flexible while maintaining compliance and continually adapting to necessary changes. Typically, more time is spent configuring the security environment just before or after the application is launched, which can cause issues between teams that have not considered security along the way. Collaboration between teams is crucial to an organisation's business efficiency.
Benefits of DevSecOps
From the outset, there are clear security objectives that can be implemented into the development process, ensuring that coding, testing guidelines, encryption, secure APIs, and state and dynamic analysis instructions are optimised. During the development process, the team will become more proficient in security, which can help identify security issues when they need to respond to a related event. Additional benefits include:
- rapid response to security changes: innovations can be delivered faster, providing the opportunity to get to market faster
cross-team collaboration: teams will be more likely to do their own work, provide training and shorten the time between handovers - earlier detection of vulnerabilities: security measures at every stage ensure greater detectability by implementing security at every stage of software development
- automation to free up time for more complex and valuable tasks
- better speed and agility for teams
DevSecOps best practices
Companies are increasingly implementing automated scanning as an aspect of CI/CD strings. However, the security debt - the number of vulnerabilities that developers have chosen not to fix - can make CI/CD results less obvious. Implementing a shift towards DevSecOps should exponentially reduce the existing vulnerability, especially with a combination of manual and automated code testing.
- Standardise and automate the environment: Every service should have as little privilege as possible to minimise unauthorised connections and access.
- Centralise user identification and access control capabilities: Strict access control and centralised authentication mechanisms are essential to secure microservices, as authentication is initiated at multiple points.
- Isolate microservices containers from each other and the network: This includes both data in transit and at rest, as both can represent high-value targets for attackers.
- Encrypting data between applications and services: A container orchestration platform with integrated security features helps minimise the risk of unauthorised access.
- Introduction of secure API gateways: Secure APIs increase authentication and path visibility. By reducing exposed APIs, organisations can reduce the attack surface.
CI/CD process security
- Integrate security scanners for containers: This should be part of the process of adding containers to the registry.
- Automate security testing in the CI process: This includes running static security analysis tools as part of compilation, and scanning pre-built container images for known security vulnerabilities when they are included in the compilation pipeline.
- Adding automated tests for security features to the acceptance testing process: Automate tests for input validation, as well as verification authentication and authorization functions.
- Automate security updates, such as patches for known security vulnerabilities: Do this with a DevOps string. This should eliminate the need for administrators to log into production systems, while creating a documented and traceable change log.
- Automate system and service configuration management functions: This allows for security compliance and eliminates manual errors. Audit and corrective actions should also be automated.
DevSecOps - summary
Security plays an increasingly important role in today's technology race and often processes and work culture determine market advantage. Therefore, DevSecOps can be part of a larger organizational goal. As Hostersi, we are happy to help you implement the DevSecOps model and assist you with your IT projects with our specialized staff and experience.





